I decided to do a write-up of the current Fireeye challenge (I am writing during the actual challenge, but the post will be released after the challenge).
To start with the challenge you need to go to http://flare-on.com and get the binary at http://flare-on.com/files/Flare-On_start_2015.exe
The binary itself is 64bit, displays a disclaimer, gets some info from your computer and drops a 2kb 32bit PE file afterwards. This 2kb file is the actual challenge level 1. I didn’t analyze the initial 64bit but I’d advise you to run it in a VM and revert the VM afterwards. I used amazon AWS because I had no 64bit VM at hand.
I ran the 2kb file called “i_am_happy_you_are_to_playing_the_flareon_challenge.exe” in Immunity Debugger. My 2nd time using Immunity actually (I used it only once during the OSCP exam, when I had to modify an exploit). So, if you are not used to debugging or don’t speak assembly language (like me) – no worries! This one is easy!
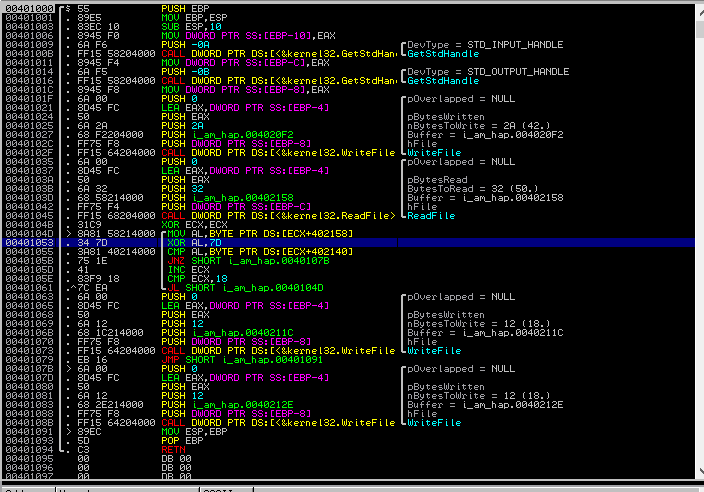
As you can see there is only one loop starting at 0040104D and ending at 00401061. The interesting operations are 0040104D until 00401055:
– MOV AL, BYTE PTR DS:[ECX+402158] takes the argument at EXC+402158 (ECX is 0 if you check the debugger) into the “lower part” of EAX. If you entered a lot of “a” you will see 0x00000061 in EAX after this command.
– XOR AL, 7D does a bitwise XOR with 0x7D on the lower part of EAX. For the ‘a’ (0x61) seen there it should create a 0x1C.
– CMP AL, BYTE PTR DS:[ECX+402140] compares the lower part of EAX (called AL) with the byte at 00402140, which should be 0x1F.
This is the main function. It takes your argument, XORes it and compares it to another value in memory. Since XOR can be reverted with another XOR we can simply take the memory at 00002140 and XOR it with 7D to get the password. Meaning 0x1F XOR 0x7D is the first character (0x62 which is b).
I have written a python program that does the job for us so you don’t have to do it manually using calc:
def sxor(s1,s2):
return ''.join(chr(ord(a) ^ ord(b)) for a,b in zip(s1,s2))
print sxor("\x1f\x08\x13\x13\x04\x22\x0e\x11\x4d\x0d\x18\x3d\x1b\x11\x1c\x0f\x18\x50", 18*"\x7d")After running it we are presented with “bunny_sl0pe@flare-” – the password to complete level 1. After sending an email to bunny_sl0pe@flare-on.com we received the binary for level 2.