TL;DR: SphinxSearch comes with a insecure default configuration that opens a listener on port 9306. No auth required. Connections using a mysql client are possible.
I recently stumbled upon SphinxSearch. A fast database that can do full-text search much faster than MySQL/MariaDB (at least in my scenario) and runs on lower ressources than Lucene, Solr or Elasticsearch (which also performed the worst in my scenario).
One thing I came accross while installing it was the default configuration. In the default configuration SphinxSearch has a listener on TCP port 9306 with no authentication. Actually authentication is not implemented in SphinxSearch as far as I know. This would make you think that this listener is at least limited to localhost? Nope. The default setup creates a listener on 0.0.0.0:9306 (reading all interfaces, any IP port 9306) and allows connections without credentials using the MySQL client.
This is a screenshot from the official documentation as of August 2019:
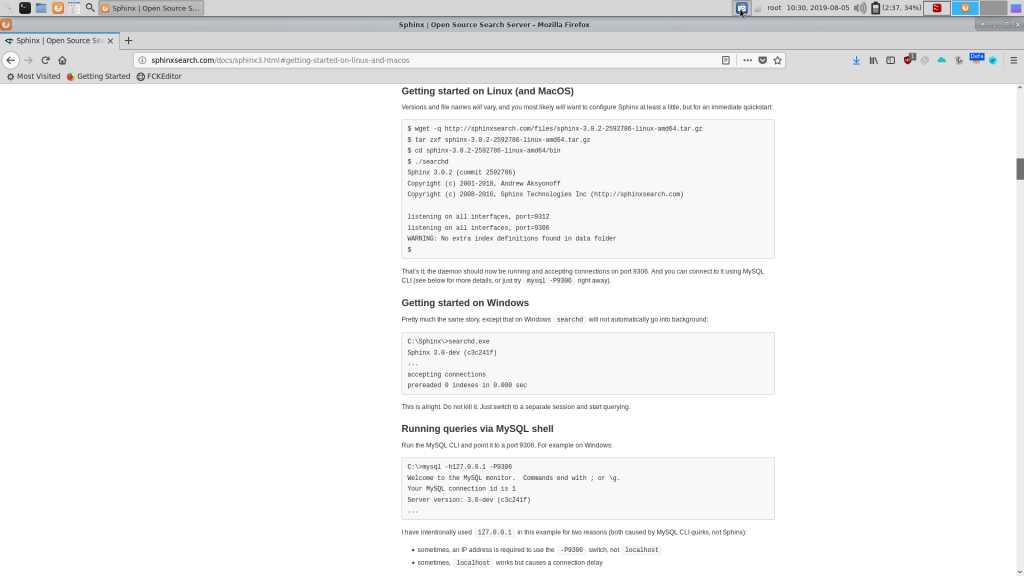
I have tried contacting the SphinxSearch team using the website form and via Skype since July, but no reply.
How to fix it?
Just go to your SphinxSearch configuration and edit the listen variable to include only localhost or put a (host) firewall like iptables in front of your installation.
Sample of a localhost listener configuration:
[..]
searchd
{
listen = localhost:9312
listen = localhost:9306:mysql41
[..]
At the time of writing the Internet has 100+ exposed installations. Some of them might be on purpose or the data might not be a secret, but for some it might be an issue. I know at least one project for email archiving which uses SphinxSearch – piler. Users should check it immediately.
This is an example of a SphinxSearch login using mysqlclient:
root@vmd292 ~/sphinx/sphinx-3.1.1/bin # mysql -P9306 -h127.0.0.1 Welcome to the MariaDB monitor. Commands end with ; or \g. Your MySQL connection id is 1 Server version: 3.1.1 (commit 612d99f) Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. MySQL [(none)]> show tables; +---------------+-------------+ | Index | Type | +---------------+-------------+ | idx1_template | local | | idx1p0 | local | | idx1p1 | local | | idx1p10 | local | | idx1p11 | local | | idx1p12 | local | | idx1p13 | local | | idx1p14 | local | | idx1p15 | local | | idx1p16 | local | | idx1p17 | local | | idx1p18 | local | | idx1p19 | local | | idx1p2 | local | | idx1p20 | local | | idx1p3 | local | | idx1p4 | local | | idx1p5 | local | | idx1p6 | local | | idx1p7 | local | | idx1p8 | local | | idx1p9 | local | | test1 | distributed | +---------------+-------------+ 23 rows in set (0.001 sec) MySQL [(none)]> quit Bye root@vmd292 ~/sphinx/sphinx-3.1.1/bin #
Hi. Thanks for pointing this out. We’re making a fork of Sphinx Search – much better supported, with monthly releases, new features (replication, PQ indexes etc.) and so on.
We’ve discussed it with the team and decided to update the defaults. Here’s the issue https://github.com/manticoresoftware/manticoresearch/issues/261
BTW in terms of security we have 2 more things:
– SSL support for http (already on github, should be released in beta stage in few days)
– another vulnerability fixed – CALL SNIPPETS() could let you read any file from the OS. https://docs.manticoresearch.com/latest/singlehtml/index.html#snippets-file-prefix fixes it. Together with the listens at 0.0.0.0 by default may be quite a breach in Sphinx.
We’ll appreciate if you ping us in case you find anything else in Sphinx/Manticore. Follow us on https://twitter.com/manticoresearch, come to our http://slack.manticoresearch.com, https://forum.manticoresearch.com and post issues on https://github.com/manticoresoftware/manticoresearch/issues
Awesome, thanks a lot for the information! I didnt know about Manticoresearch, only Sphinx. I will give it a try!
CALL SNIPPETS() sounds interesting and scary at the same time…
https://github.com/manticoresoftware/manticoresearch/issues/261 has been fixed.